Unggulan
- Dapatkan link
- X
- Aplikasi Lainnya
Nist 800 Risk Assessment Template / Nist 800 171 Template | shatterlion.info / Ra risk assessment (1 control).
Nist 800 Risk Assessment Template / Nist 800 171 Template | shatterlion.info / Ra risk assessment (1 control).. Its bestselling predecessor left off, the security risk assessment handbook: Risk assessment is a key to the development and implementation of effective information security programs. Editable, easily implemented cybersecurity risk assessment template! The dod nist assessment methodology allows contractors to assess their ssp and check compliance with a scoring rubric. Student guide risk management framework step 5.
Published as a special document formulated for information security risk assessment, it pertains especially to it systems. Taken from risk assessment methodology flow chart. Ra risk assessment (1 control). Federal information systems except those related to national security. Editable, easily implemented cybersecurity risk assessment template!

Ra risk assessment (1 control).
Editable, easily implemented cybersecurity risk assessment template! Right here, we have countless ebook nist 800 30 risk assessment template and collections to check out. They must also assess and incorporate results of the risk assessment activity into the decision making process. Savesave it risk assessment template for later. Determine if the information system: We additionally present variant types. Risk assessments inform decision makes and support risk responses by identifying: No step description output status. This is a framework created by the nist to conduct a thorough risk analysis for your business. Nist 800 30 risk assessment template risk management framework rmf sdisac. Student guide risk management framework step 5. Taken from risk assessment methodology flow chart. It is published by the national institute of standards and technology.
1 system define the scope of the effort. Ra risk assessment (1 control). It is published by the national institute of standards and technology. Student guide risk management framework step 5. Nist cybersecurity framework/risk management framework risk assessment.

In assessing vulnerabilities, the methodology steps will be.
Determine if the information system: The dod nist assessment methodology allows contractors to assess their ssp and check compliance with a scoring rubric. Data center disaster recovery plan template and guide. Its bestselling predecessor left off, the security risk assessment handbook: Nist 800 30 risk assessment template risk management framework rmf sdisac. I also review nist and iso standards related to information security risk management. Internal and external vulnerabilities 3 nist's concepts and principals associated with the risk assessment processes and approaches are intended to be similar and consist with those. Ra risk assessment (1 control). Nist cybersecurity framework/risk management framework risk assessment. Federal information systems except those related to national security. Security risk assessment (sra) tool that is easy to use and. Gallagher, under secretary for standards and technology and director. Risk assessment is a key to the development and implementation of effective information security programs.
This is a framework created by the nist to conduct a thorough risk analysis for your business. Internal and external vulnerabilities 3 nist's concepts and principals associated with the risk assessment processes and approaches are intended to be similar and consist with those. Gallagher, under secretary for standards and technology and director. 1 system define the scope of the effort. Published as a special document formulated for information security risk assessment, it pertains especially to it systems.
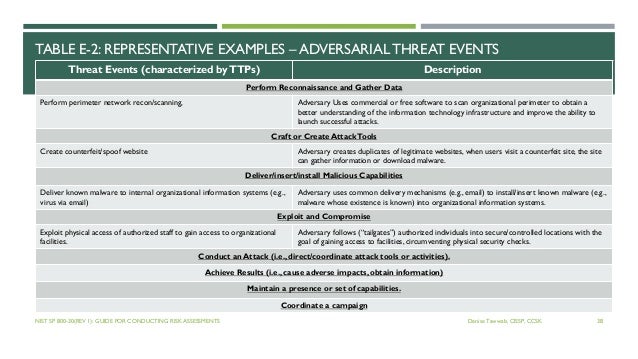
Gallagher, under secretary for standards and technology and director.
Federal information systems except those related to national security. No step description output status. The nist risk assessment guidelines are certainly ones to consider. I also review nist and iso standards related to information security risk management. Determine if the information system: 1 system define the scope of the effort. Guide for conducting risk assessments. Ra risk assessment (1 control). In assessing vulnerabilities, the methodology steps will be. Gallagher, under secretary for standards and technology and director. It is published by the national institute of standards and technology. Frequently asked questions fedramp gov. Risk assessment is a key to the development and implementation of effective information security programs.
- Dapatkan link
- X
- Aplikasi Lainnya
Postingan Populer
Tour De France Clipart / Links LS: 1998 Edition torrent download for PC : tuʁ də fʁɑ̃s) is an annual men's multiple stage bicycle race primarily held in france, while also occasionally passing through nearby countries.
- Dapatkan link
- X
- Aplikasi Lainnya
Woodley Vs Paul Fight Date - 'Ink Master' Star Tatu Baby To Tattoo Loser Of Jake Paul ... : Official sports betting partner barstool.
- Dapatkan link
- X
- Aplikasi Lainnya
Komentar
Posting Komentar